 A few days ago Apple became aware of a vulnerability in both their iOS and OS X platforms that can allow users to become a victim of a man-in-the-middle (MITM) attack that can compromise any secure data being sent via Wi-Fi. The fix can be done as easily as updating your device, but there’s a little more involved to get a handle on this new Apple security flaw.
A few days ago Apple became aware of a vulnerability in both their iOS and OS X platforms that can allow users to become a victim of a man-in-the-middle (MITM) attack that can compromise any secure data being sent via Wi-Fi. The fix can be done as easily as updating your device, but there’s a little more involved to get a handle on this new Apple security flaw.
What’s This Security Flaw All About?
MITM, or Man-In-The-Middle is a style of attack that is kind of like eavesdropping on a private conversation actively. Basically the attacker makes a connection to your computer and passes any information your computer would send out to the world first through his or her machine to pull important pieces of information out before sending it on its way. Think of a mailman opening every letter, reading everything and recording the bits he found interesting or worth money, then sealing the envelopes and sending them on their way again, effectively becoming the man in the middle.

This is done by connecting via an SSL (Secure Socket Layer) connection to your machine when you’re on a public Wi-Fi connection. The web uses SSL certificates to know who to trust and who not to trust, just like a police badge of sorts. When Apple built their SSL verification they didn’t make it require your browser to verify the hostname of the person using the certificate, meaning it could be tricked. In other words, it’s like someone saying “Yea, I’m a cop” and you not checking for a badge or other identification.
What Does This Mean For You?
Well, what this means for you is that you need to update all of your iOS devices right now. iOS 6 and 7 both are receiving updates for this with iOS 7.0.6 and 6.1.6, respectively. If you send unencrypted information over an unsecured network like public Wi-Fi without doing this update, your data could be stolen and used. This means credit card numbers, personal data, and login information. Updating is easy and since this is a non-major update it can be done quickly and easily over the air right from your device. Here is a tweet from Ashkan Soltani showing a few apps that are affected by this:
Here are some of the apps which rely on the vulnerable Apple #gotofail SSL library beyond Safari /cc @a_greenberg pic.twitter.com/ombDOOa01A — ashkan soltani (@ashk4n) February 23, 2014
Another tweet from Matthew Green, a cryptology professor at Johns Hopkins University warns of the issue as well:
I’m not going to talk details about the Apple bug except to say the following. It is seriously exploitable and not yet under control. — Matthew Green (@matthew_d_green) February 21, 2014
How To Fix The Security Flaw
The updating procedure is fairly easy to accomplish. On your iOS device (6 and 7 are basically the same in this regard) go into Settings, then tap on General. Once here, tap on Software Update. You’ll see the new version, just tap Download and Install to complete the process.
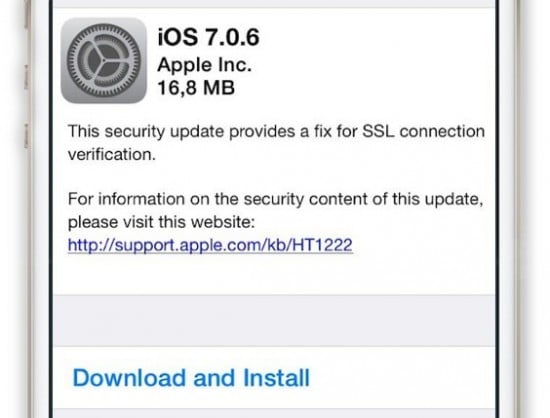
Your iPhone, iPad, or iPod Touch will download and install the ~35MB update and once your device restarts, it should be safe and good to go. Head back to the Software Update screen if you want to verify the patch is applied. If it says iOS 7.0.6 then you’re done. If you’re one of the lucky ones that has access to the beta of iOS 7.1 the news isn’t so bright. Currently Apple doesn’t have a fix out for the beta release of it’s next mid-cycle operating system update. If you’re using an iOS device running 7.1 now, it might be wise to downgrade until a fix is found, or at least stop using Wi-Fi until you can update the software.
What About My Mac?
 At the beginning I mentioned this is affecting both iOS and OS X devices. As of the time of writing this, Apple has not released an update for Macs yet. This means that your Mac is 100% in danger of this attack. You can abate any issues by making sure you don’t connect to any public Wi-Fi before a fix is found, but other than that the issue exists until Apple fixes it. We should see an update to OS X in the very near future, as Apple is taking this threat very seriously, releasing an iOS update only a week or so after a small update meant mostly for Chinese iPhones.
At the beginning I mentioned this is affecting both iOS and OS X devices. As of the time of writing this, Apple has not released an update for Macs yet. This means that your Mac is 100% in danger of this attack. You can abate any issues by making sure you don’t connect to any public Wi-Fi before a fix is found, but other than that the issue exists until Apple fixes it. We should see an update to OS X in the very near future, as Apple is taking this threat very seriously, releasing an iOS update only a week or so after a small update meant mostly for Chinese iPhones.
What’s Next?
Well, what should be next for you is to update any iOS devices you have that are running iOS 6 or 7. The error did not exist in iOS 5, so those are safe. OS X Mavericks is the only OS X that has the SSL issue, so it will ultimately be the only one upgraded. Until an update is available, stay off of Wi-Fi and other people’s networks as much as possible and better yet, just take a little time off from using the Internet on your Mac until the patch is released.





2 thoughts on “How To Fix the Latest Apple Security Flaw”
For many many people, this issue is becoming way overblown. We haven’t seen any actual attacks using this. It’s been there for a while, and it’s an OpenSSL bug even. It’s not even going to affect the vast majority of users, and open wifi networks are already considered a security hole.
MITM attacks aren’t that easy to pull off.
I’ll have to disagree with you on this point. While it’s not easy to pull of a MITM attack, all you need is one and you’re done for. We haven’t seen any attacks that we know of. I imagine if some less than legal people knew of this they weren’t telling the world and were using it to gain information from unsuspecting users.
When a vulnerability like this becomes widely known the need to update it ASAP becomes even more necessary. For people who live out of their Macs and iPhones, losing that information could be a complete disaster.